bali & pari Malvina Modern Bohemian Natural Brown Rattan Queen Size Wall-Mount Headboard - Walmart.com

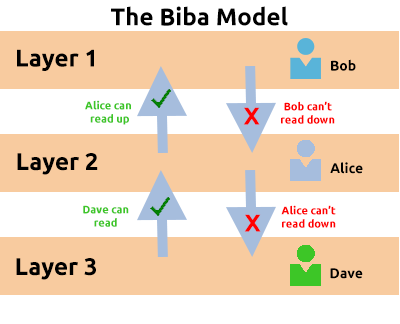
An Introduction to Multi-level Security Confidentiality: Clark-Wilson and Brewer Nash Models vs Bell-Lapadula and Biba Models – Umar's Blog
Evaluation of the Appropriateness of Trust Models to specify Defensive Computer Security Architectures for Physical Protection S

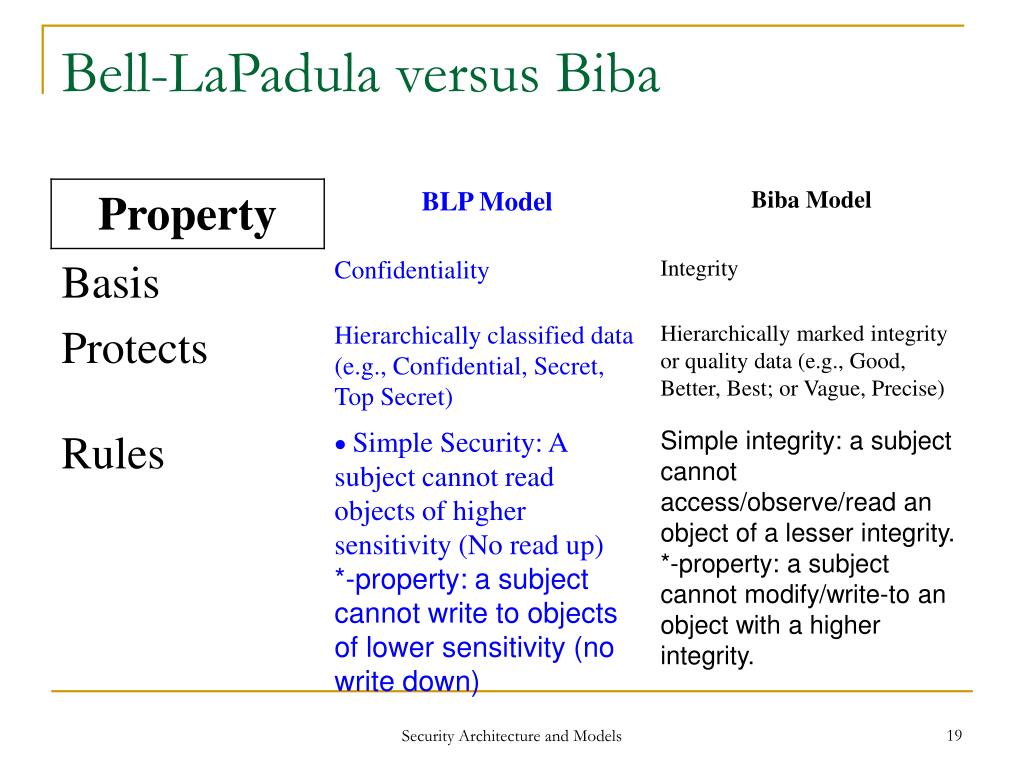
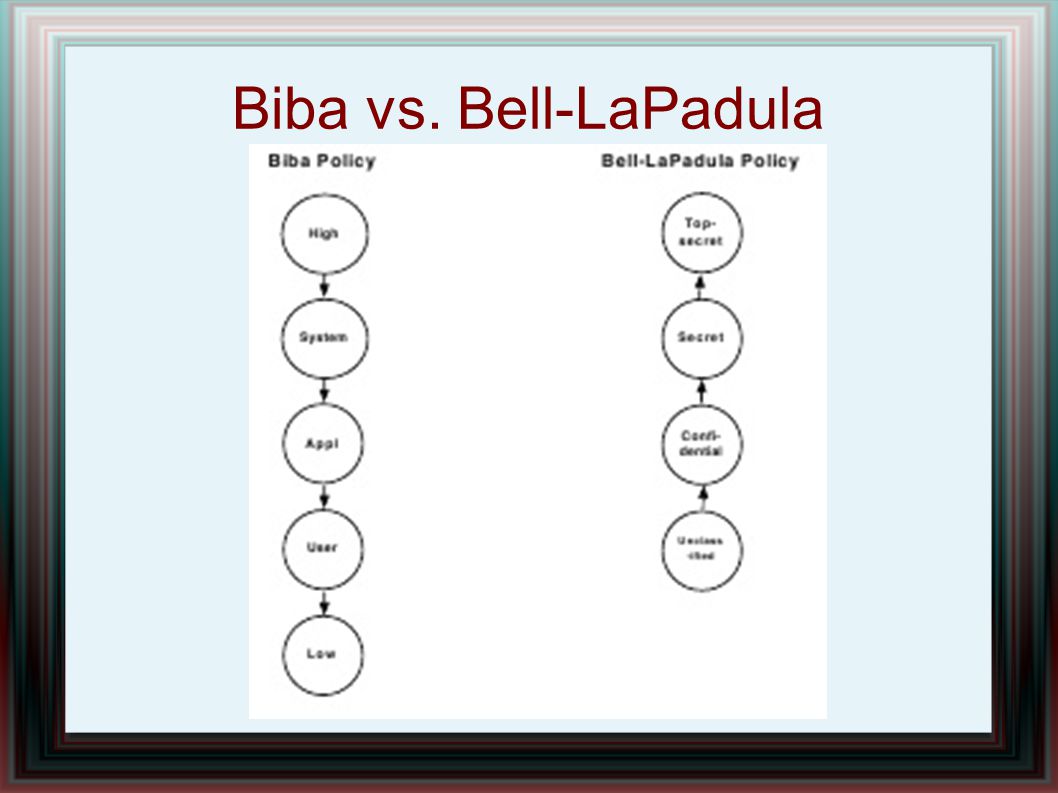
Session 2 - Security Models and Architecture. 2 Overview Basic concepts The Models –Bell-LaPadula (BLP) –Biba –Clark-Wilson –Chinese Wall Systems Evaluation. - ppt download