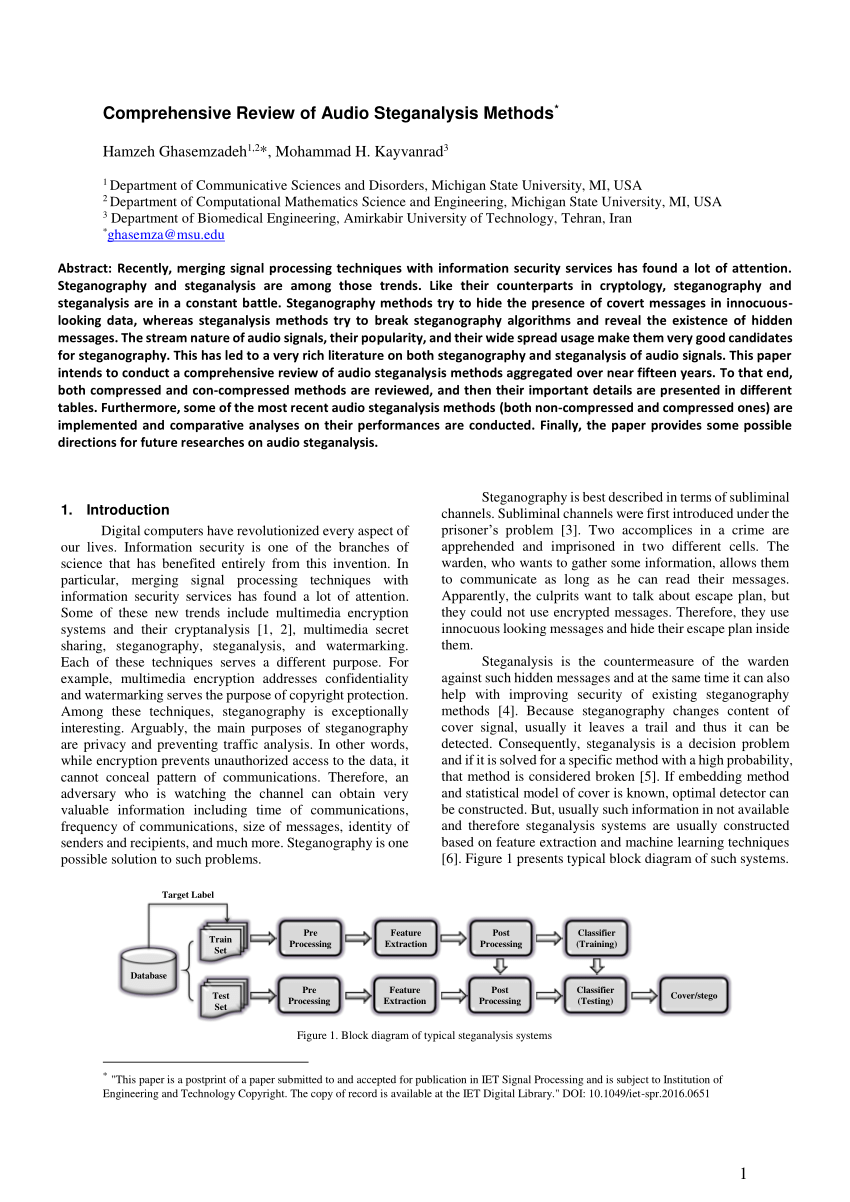
Steganalysis of convolutional neural network based on neural architecture search | Multimedia Systems

Steganalysis of convolutional neural network based on neural architecture search | Multimedia Systems

Steganalysis of Very Low Embedded JPEG Image in Spatial and Transform Domain Steganographic Scheme Using SVM | SpringerLink

Dataset mismatched steganalysis using subdomain adaptation with guiding feature | Telecommunication Systems

UNCOVER: Development of an efficient steganalysis framework for uncovering hidden data in digital media

PPT - jessica FRIDRICH jan KODOVSK Ý miroslav GOLJAN vojt ě ch HOLUB PowerPoint Presentation - ID:1908439

Dataset mismatched steganalysis using subdomain adaptation with guiding feature | Telecommunication Systems

Digital image steganography survey and investigation (goal, assessment, method, development, and dataset) - ScienceDirect
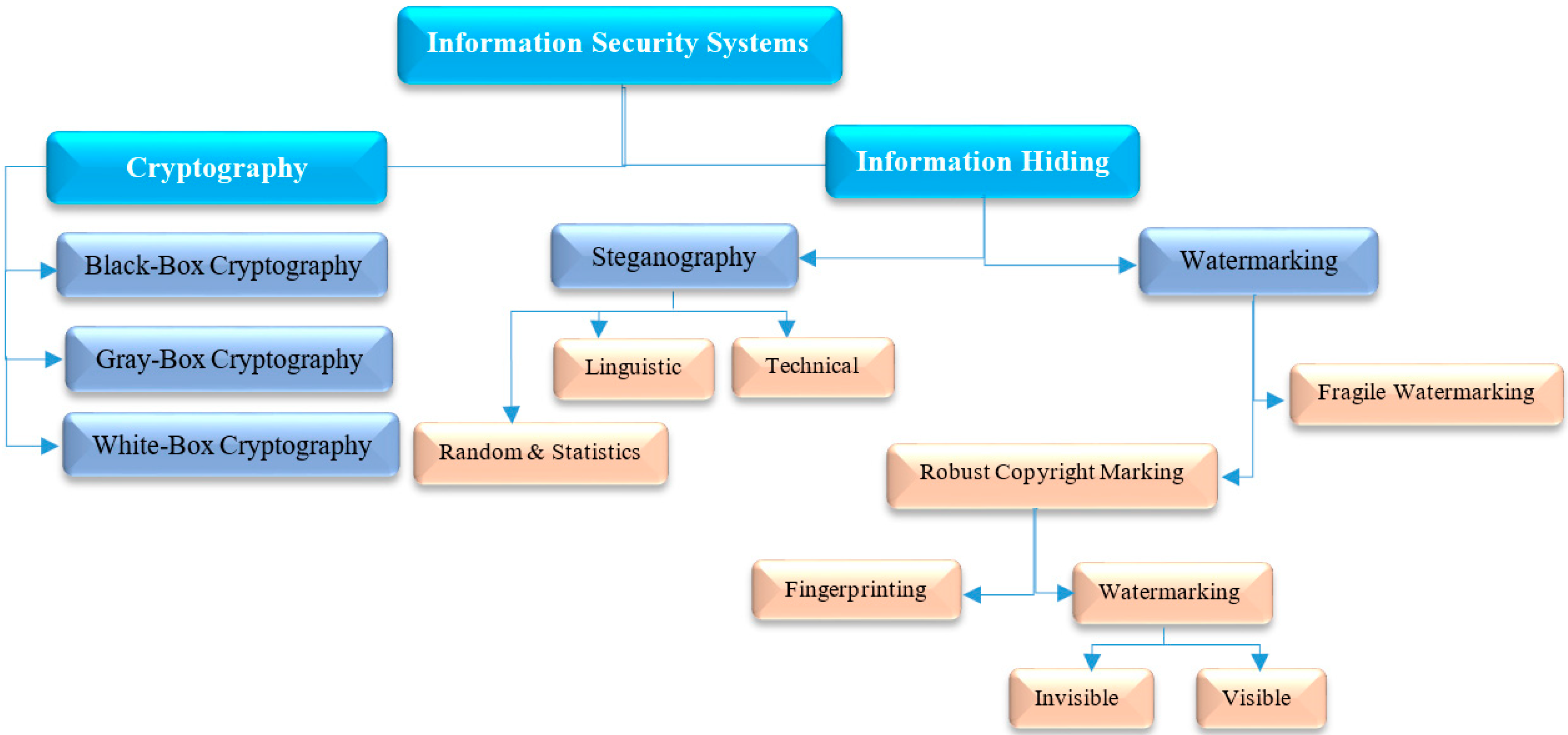
Entropy | Free Full-Text | Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis

Mathematics | Free Full-Text | Steganography with High Reconstruction Robustness: Hiding of Encrypted Secret Images
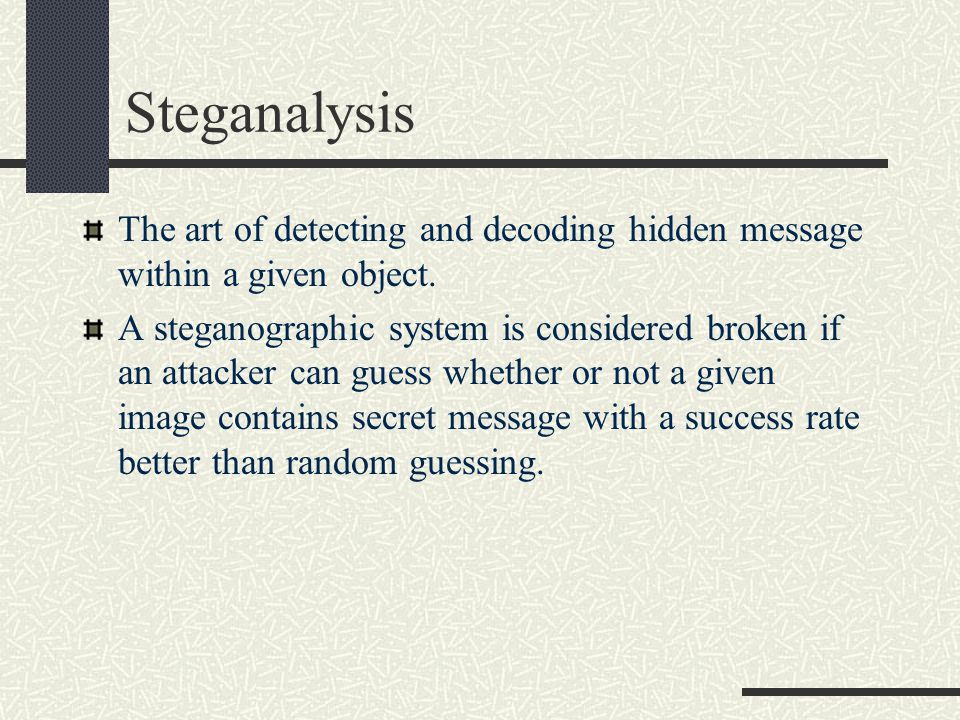
Steganography - A review Lidan Miao 11/03/03. Outline History Motivation Application System model Steganographic methods Steganalysis Evaluation and benchmarking. - ppt download

Steganalysis of JSteg algorithm using hypothesis testing theory | EURASIP Journal on Information Security | Full Text

CNN-based steganalysis and parametric adversarial embedding:A game-theoretic framework - ScienceDirect

PDF) A Generative Learning Architecture Based on CycleGAN for Steganalysis with Unpaired Training Images
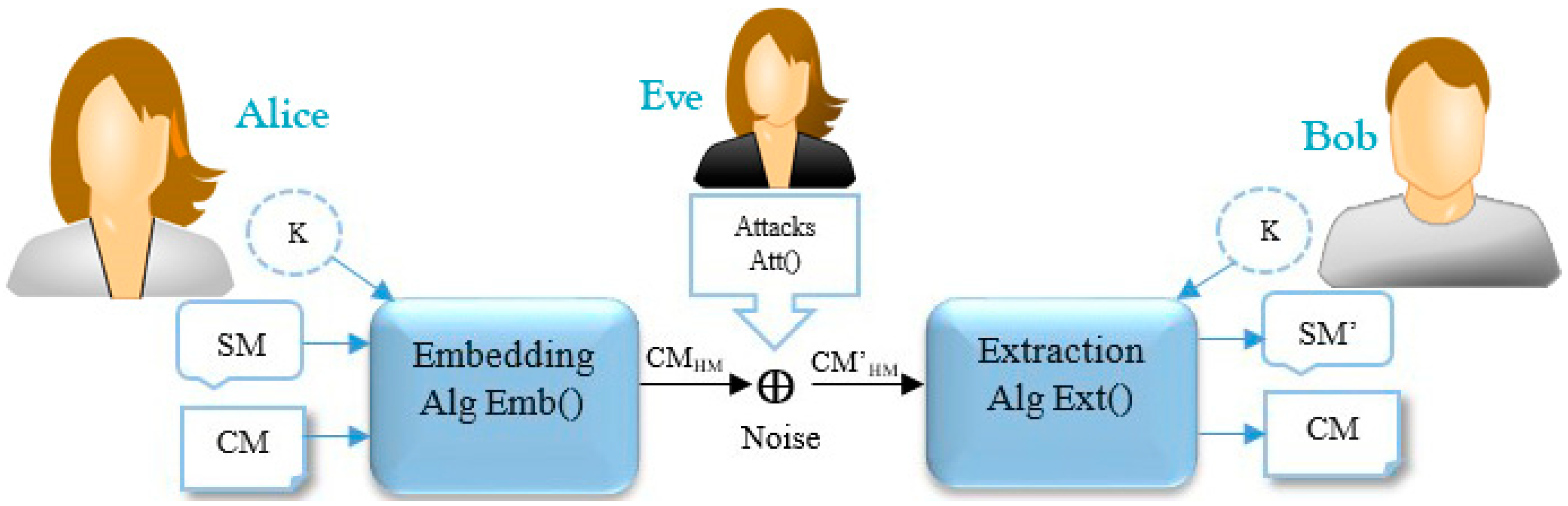



![PDF] StegoNet: Turn Deep Neural Network into a Stegomalware | Semantic Scholar PDF] StegoNet: Turn Deep Neural Network into a Stegomalware | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6c141b0c8916527fb85590331c1f0fe8b91f819e/9-Figure6-1.png)